CyberRansom ... Be Prepared
"It [AI-powered computer program ChatGPT] has the ability for someone with not very much skill set or maybe even not a great command of the English language to create a full, almost flawless script to use in an attack against somebody in a phone scam or an email phishing scam or what have you.""In the past, [hackers and scammers] would rely on their own grammar and spelling skills, which often many people were able to identify and say, 'oh, that looks like a scam'. They're getting harder and harder to detect now.""They're either using phishing or an even more advanced version of phishing, called whaling, where ... it looks like it's coming from an executive instructing his workers to do XYZ. And as soon as they open or click or do anything in that email, they end up infecting the organization."Robert Falzon, head, engineering, cybersecurity firm Check Point Canada"They're increasing across western democracies. This is a serious problem, a serious challenge, that is becoming increasingly severe."It's supported by sovereign countries that harbour ransomware attackers, and ransomware attacks have proven to be highly lucrative.""The more important the organization, the more critical that organization is to the proper functioning of society or the economy, the more likely it is that a ransomware gang will be able to leverage significant financial return. So the attack on SickKids hospital is exactly the kind of attack that we need to expect."Charles Finlay, founding executive director, Rogers Cybersecure Catalyst Centre, Toronto Metropolitan University
 |
| Global cyber futuristic financial network security concept. Fast speed internet connection blocked. Getty |
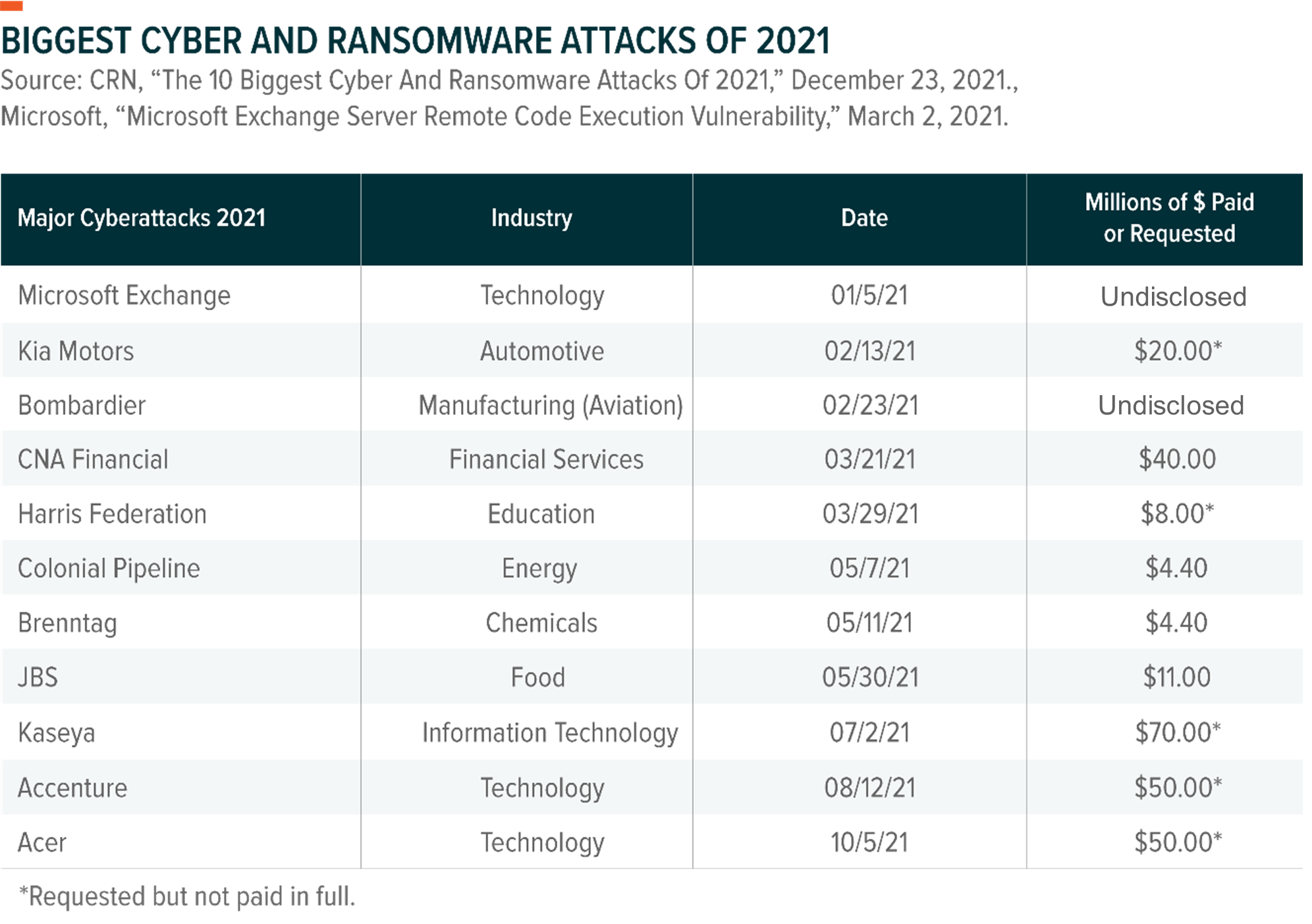
The increasing cyberattacks hitting government agencies, corporations, hospitals and other vulnerable-to-attack groups has had the effect of shutting down services in critical arenas while the entities struck by attack desperately address themselves to solving their vulnerabilities. Social media sites are not immune to these attacks, and it seems, no one group or individual is. In the case of foreign governments known to indulge in cyberattacks focusing on the military or government the source is well known and the threat potential enormous.
Recently in Canada a number of high-profile cyberattacks has seen hospitals, businesses and organizations, including the Liquor Control Board of Ontario and the Hospital for Sick Children in Toronto along with Scouts Canada, become the focus of cyberattacks. Experts on cybersecurity are agreed; the frequency of these attacks mounted both by hostile governments and criminal groups is on the increase. Part of that is attributable to the fact that more and more business is conducted online; we're increasingly dependent on technology..
And as governments at every level along with corporations and manufacturers, universities and hospitals become ever more reliant on infrastructure, networking and communications online their vulnerability is on the increase. Even while all these groups continually upgrade their security. Intrusive software is continually being upgraded as well, enabling even amateur computer crooks to become more capable and versatile in the engineering of cyberattacks.
Access to new technology aiding the development of malware, scripting and associated tools potential hackers make use of like the AI-powered computer program ChatGPT are all put to unscrupulous use. The cyberattack that hit Sick Children's Hospital in Toronto affected phone lines, internal clinical systems and disrupted laboratory and imagining results. Any organization believed vulnerable to a ransom leverage attracts hackers.
Many of the tools that enable cyberattacks take a scattered approach in sending out email to thousands of potential victims. "These are incidental attacks where somebody unfortunately falls victim to either clicking on a phishing email or an attachment or something, and then it infected that system in that area. And now you've got a widespread problem", pointed out Check Point's Falzon.
So what do the experts in cybersecurity recommend? Nothing anyone who uses a computer doesn't already know; keep computers and mobile devices updated with critical software since manufacturers create frequent "patches and updates" targeting vulnerabilities in their products. Passwords should be updated often, and never used for more than a single site or service. Become hyper-aware of emails or text messages from unknown sources.
"Somebody could send you a text, whether it's WhatsApp, for example, where a single text [is] sent to your cellphone, you view it, and next thing you know you're vulnerable.""They can control your camera, your microphone, to see where you are, read your text messages, things like that.""It's a massive risk to carry them around and not have any protection on them."Robert Falzon, Check Point Canada cybersecurity
Labels: Cyber Threats, Cyberattacks, Cybersecurity

0 Comments:
Post a Comment
<< Home